It's a new week, which means that it's time for a new Windows 10 Insider Preview build. This week's PC build in the Fast ring is 16232, and there are some new features.
Just like the ones that came before it, build 16232 is from the Redstone 3 Development Branch, meaning that it's a preview of the Fall Creators Update. And this isn't the first time that an RS3 build has included new features - builds 16215 and 16226 were jam-packed with new front-facing features.
Here's what's new:
Windows Defender Application Guard (WDAG) Improvements:
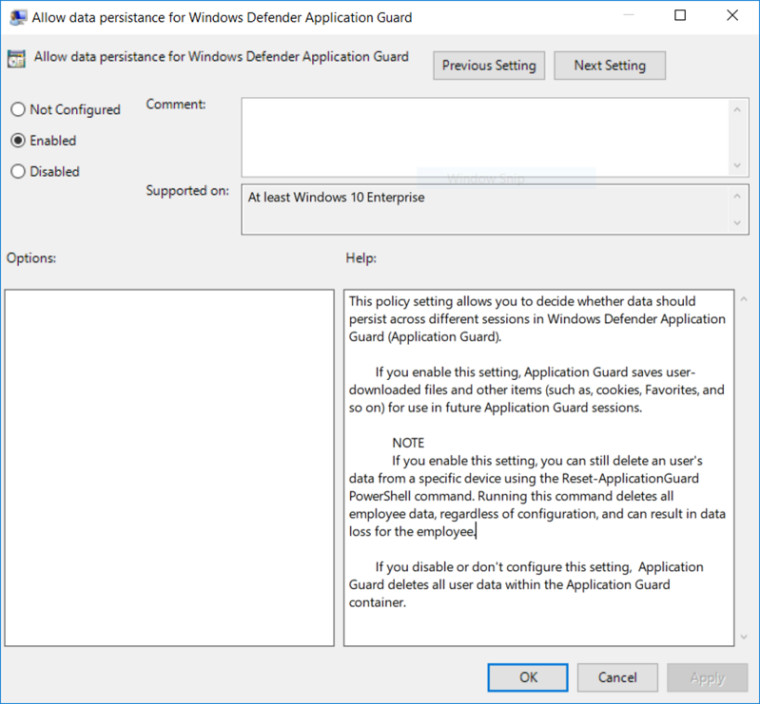
Giving you access to all the rich features in Microsoft Edge while using Application Guard: Building on our work in Build 16188, we have added support for Microsoft Edge data persistence while using Application Guard. Once enabled, data such as your favorites, cookies, and saved passwords will be persisted across Application Guard sessions. The persisted data will be not be shared or surfaced on the host, but it will be available for future Microsoft Edge in Application Guard sessions.
How to take advantage of Data Persistence when using Microsoft Edge with Application Guard: You enable Data Persistence for Microsoft Edge in Application Guard using Group Policy. Note that Data Persistence for Application Guard with Microsoft Edge sessions is not enabled by default. To enable data persistence, close all Microsoft Edge windows and update the Windows Components > Windows Defender Application Guard policy to turn on data persistence:
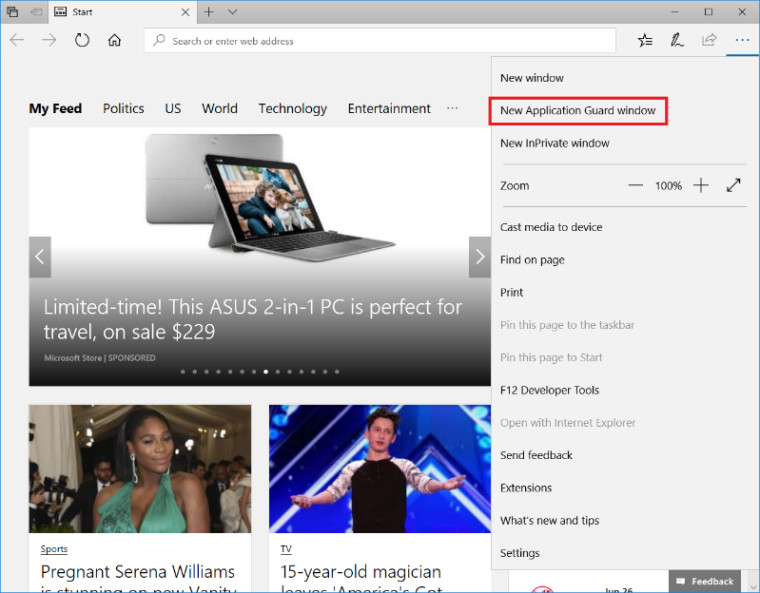
After the Group Policy settings are set, next launch New Application Guard Window from the Microsoft Edge menu:
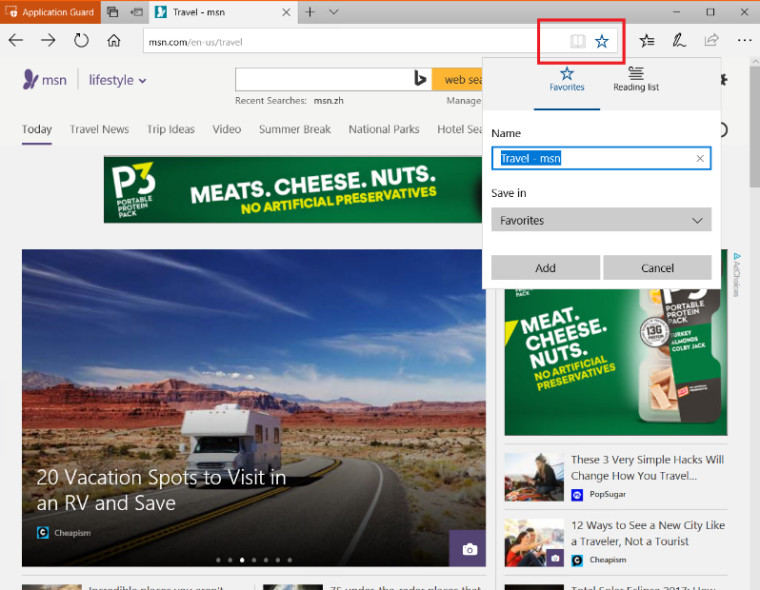
Then browse to your favorite web site and add it to Favorites in Microsoft Edge as shown here:
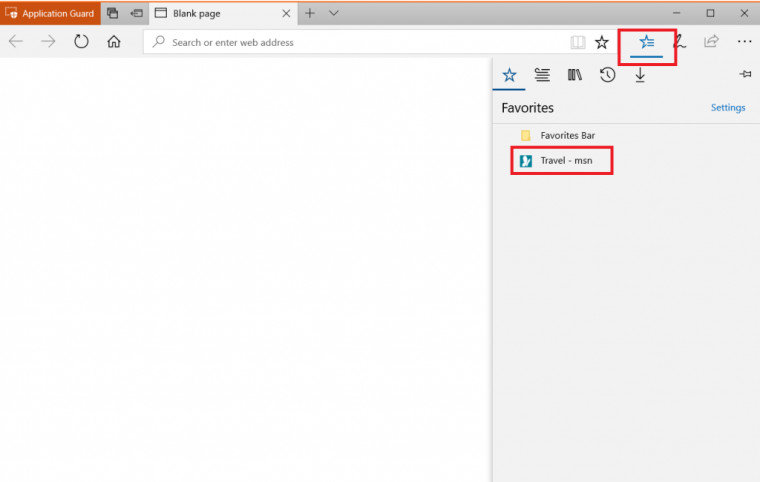
How to find your Favorites after you close Edge with Application Guard:Since you have enabled Data Persistence using Group Policy for Application Guard, the site you saved to your Favorites will be available for later use, with Microsoft Edge in Application Guard, even after reboots as well as build to build upgrades of Windows.
Read more about what the Windows Defender Application Guard team has been working on in this latest Insider Preview by visiting this community page
To learn more about what’s coming in Windows Defender Application Guard, please take a look at this new Microsoft Mechanics video.
Introducing Exploit Protection:
We’ve heard your feedback regarding the upcoming EMET EOL, so we’re excited to announce that starting with this build you can now audit, configure, and manage Windows system and application exploit mitigation settings right from the Windows Defender Security Center! You don’t need to be using Windows Defender Antivirus to take advantage of these settings.
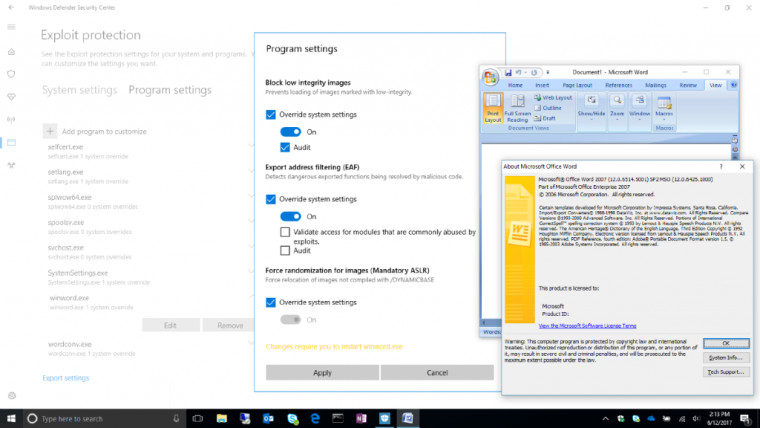
After upgrading to this build, you can find these settings by opening the Windows Defender Security Center and going to the App & browser control page:
Either right-click the icon in the notification area on the taskbar and click Open, or search via the Start menu for Windows Defender Security Center
From Windows Defender Security Center, click on App & browser controland then scroll to the bottom of the resulting screen to find Exploit Protection
More detailed documentation will follow on Microsoft Docs, and remember that Exploit Protection is a work-in-progress and might not be fully functional just yet!
Introducing Controlled folder access in Windows Defender Antivirus:
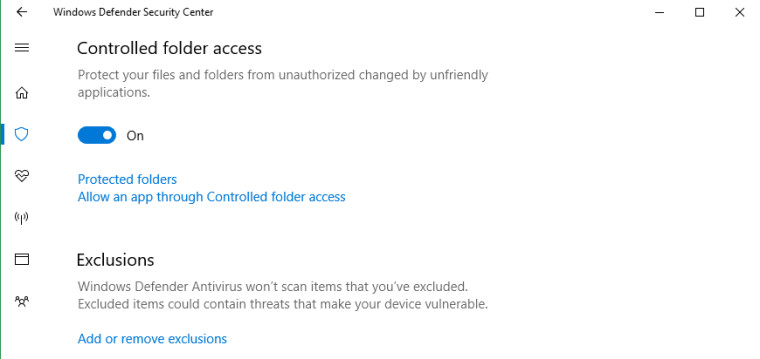
In this build, we’re making it easier for you to protect valuable data from malicious apps and threats, such as ransomware. To enable the feature, search for and open the Windows Defender Security Center from Start, go to the Virus & threat protection settings section, and set the switch to On:
Controlled folder access monitors the changes that apps make to files in certain protected folders. If an app attempts to make a change to these files, and the app is blacklisted by the feature, you’ll get a notification about the attempt. You can complement the protected folders with additional locations, and add the apps that you want to allow access to those folders.
Allowing apps can be useful if you’re finding a particular app that you know and trust is being blocked by the Controlled folder access feature. Click Allow an app through Controlled folder access and locate and add the app you want to allow.
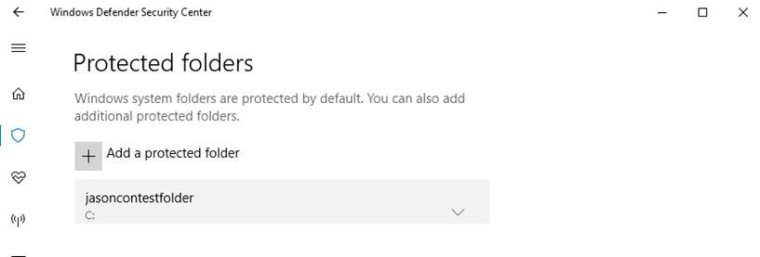
You can add additional folders to the list of protected folders, but you cannot alter the default list, which includes folders such as Documents, Pictures, Movies, and Desktop. Adding other folders to Controlled folder access can be handy, for example, if you don’t store files in the default Windows libraries or you’ve changed the location of the libraries away from the defaults.
Click Protected folders in the Controlled folder access area and enter the full path of the folder you want to monitor. You can also enter network shares and mapped drives, but environment variables and wildcards are not supported (for right now).
As you can see, a big focus of this build is security and Windows Defender features.
Microsoft also notes that Insiders won't be receiving updates for apps that come with Windows, as the firm needs to test the apps that will come pre-installed when the Fall Creators Update ships. This is similar to what the company did a couple months before releasing the Creators Update.

















18 Comments - Add comment