
A new strain of Trojan malware for the Android operating system has recently been discovered, which deceives unsuspecting users into downloading a fake update for Adobe Flash player, silently downloading more malware once it is activated.
Detected by security firm ESET, the malicious software labeled as "Android/TrojanDownloader.Agent.JI" targets all versions of Android. It is distributed through social media, as well as compromised websites, usually comprised of adult-themed pages. The malware displays a legitimate-looking update screen, prompting the user to download an update for the device's Adobe Flash player in order to stay safe online.
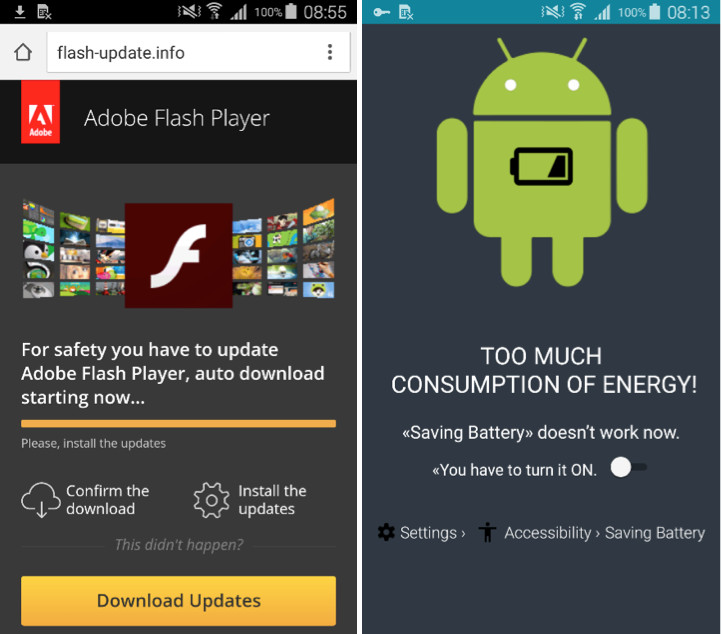
If the user falls for the fake message, another prompt will be displayed, this time an alert about too much consumption of the battery. The page claims that in order to fix this, they must activate a "new 'Saving Battery' mode." The pop-up further claims that the user's current power saving mode is no longer working, and the message will keep appearing until its endorsed battery mode is enabled.
Should the user finally accept its demands, they will be redirected to a legitimate Android Accessibility settings page. It will display real services used by the system, but it also includes a "Saving Battery" option, which is created by the malware.
This will now request permissions to monitor the user's actions on the phone, retrieve window content, and turn on explore by touch. All of these are required for the attacker to mimic the user's clicks, and select anything on the screen.
Once all of this is done, the Flash player pop-up will disappear. However, the malware will now contact its Command & Control (C&C) server, providing the compromised device's details. After a successful connection has been established, the server will download more apps onto the device, ranging from adware, spyware, and even ransomware. In order for the victim to not interfere with this process, the malware will display a fake lockscreen which cannot be dismissed.
After the download process, the lockscreen will finally disappear, and the user is free to use the device as they wish. However, at this point, due to the installed apps, the unsuspecting owner will now be spied on regarding their activity.
To remove Android/TrojanDownloader.Agent.JI, one must uninstall the downloader from the Settings app. However, this does not get rid of the other downloaded apps. "Unfortunately, uninstalling the downloader doesn't remove malicious apps the downloader might have installed. As with the downloader itself, the best way for cleaning up the device is using a mobile security solution," says Lukáš Štefanko, an ESET malware researcher.
In order to stay safe, it is recommended to not install raw APK files downloaded from the web, as they may contain malware. It must also be known that Flash player support for Android has been discontinued since 2012 due to stability and security issues, meaning that it is no longer used for the mobile web today, and any pop-up claiming that an update is needed is a complete hoax.
Source: We Live Security via ZDNet
















14 Comments - Add comment