
Microsoft Defender will now block all incoming and outgoing communication from a compromised and unmanaged Windows device. Microsoft Defender for Endpoint (MDE) has gained a new feature that attempts to slow down and possibly halt attackers from moving laterally across the network using compromised unmanaged devices.
Administrators managing devices running Windows which may or may not be protected by Microsoft Defender for Endpoint will now be able to “contain” specific computers. This new capability gives network administrators the ability to restrict the movement of data, information, and commands from a device that may be compromised by hackers. Interestingly, Admins will be able to restrict information flow even from devices that are not protected by the MDE:
Starting today, when a device that is not enrolled in Microsoft Defender for Endpoint is suspected of being compromised, as a SOC analyst, you will be able to 'Contain' it. As a result, any device enrolled in Microsoft Defender for Endpoint will now block any incoming/outgoing communication with the suspected device.
It is no secret that hackers go after weak and unmanaged devices. Once such devices are compromised, hackers have a lot more freedom to move laterally within a network. Microsoft claims 71% of human-operated ransomware attacks are started by hacking an unmanaged device.
Windows devices that are part of the MDE environment can be easily isolated to prevent hackers from compromising other devices in the network. However, quickly isolating a device that isn't protected by MDE often proves difficult. The delay can prove costly as hackers may have already compromised other devices.
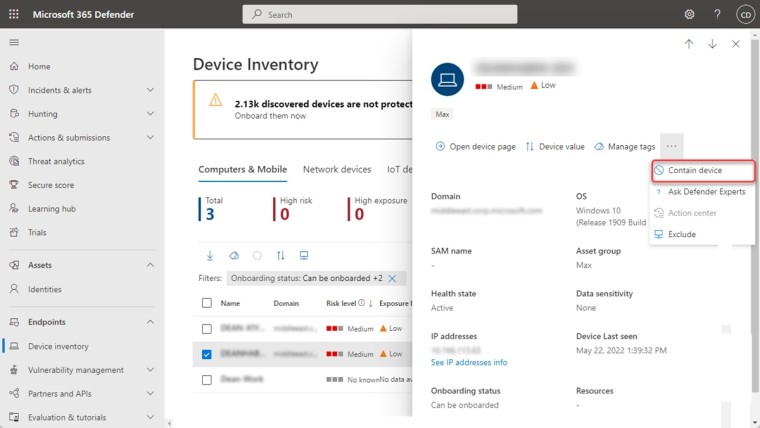
The new feature basically instructs any device protected by MDE to restrict incoming and outgoing communication with a device that is suspected of being compromised. It is not immediately clear if Microsoft Defender for Endpoint could independently flag a device as suspicious and instruct other MDE-enrolled devices to block data flow. For the time being, an Admin will have to contain the compromised device.
The new functionality is only supported on devices running Windows 10 and Windows Server 2019+ devices that are protected by Microsoft Defender for Endpoint.

_small.jpg)















1 Comment - Add comment