A new strain of malware has recently been discovered spreading on Facebook, taking advantage of innocent-looking image files to infect computers.
Discovered by Bart Blaze, a security researcher, the malware takes the form of .SVG image files, which are sent from compromised Facebook accounts. SVG image files, unlike other common file types, have the ability to contain embedded content like JavaScript, and can be opened in a modern browser. 
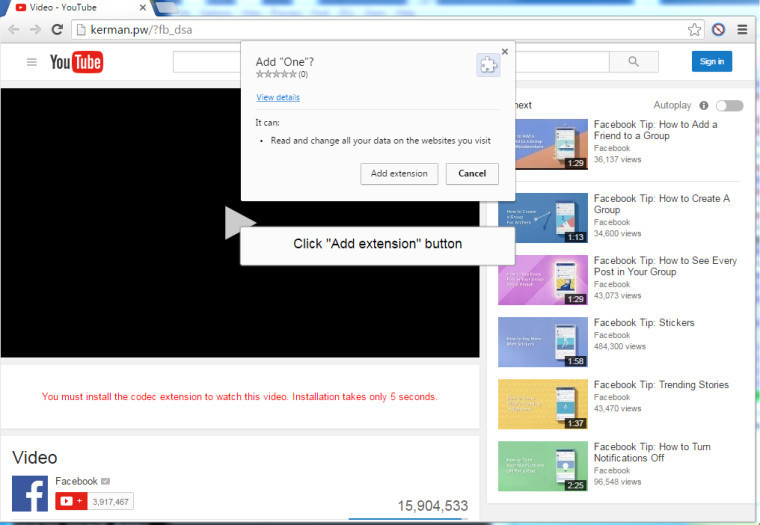
With the malicious item in question, clicking on the image redirects the user into a website posing as YouTube. While it might not immediately raise red flags upon entering the fake website, the page will then ask the user to download a certain codec extension in Google Chrome in order to view the video, a very typical modus of malware creators.
Installing the purported extension will give it the capability to alter users' data regarding websites they visit. According to Blaze, the extension will also spread the malware further on Facebook, compromising the victim's account.
To make things worse, Peter Kruse, a colleague of Blaze, further noted that in another instance, the image file contained the Nemucod downloader, which then downloaded a copy of Locky ransomware.
It is not known how the SVG files bypassed Facebook's file extension filter, which only accepts a set number of extensions, but Facebook's security team has been reportedly notified of the exploit. The malicious Chrome extension has also been removed.
As per usual, it pays to be wary of what we click on the internet, as it may lead us to websites that could possibly compromise our data and identity. Malware on Facebook is nothing new, with cybercriminals trying hard to fool its users through various methods, so taking an extra step in keeping yourself and others protected can go a long way.
Update: Facebook reached out to Neowin to clarify the issue, stating that according to their own research, they found that the malware was not in any way connected to Locky or other types of ransomware, and it only has the ability to propagate itself on the social network.
“We maintain a number of automated systems to help stop harmful links and files from appearing on Facebook, and we are already blocking these ones from our platform. In our investigation, we determined that these were not in fact installing Locky malware—rather, they were associated with Chrome extensions. We have reported the bad browser extensions to the appropriate parties.”
Moreover, the impact of the issue is reportedly limited to a number of users, and that if Facebook detects suspicious behavior on an account, the user will be notified the next time they login. "We will keep improving our systems to ensure that people continue to have a safe experience on Facebook," the company said.
Source and Images: Bart Blaze via Help Net Security
















12 Comments - Add comment