Chances are if you are reading this, that you're pretty clued in on all things Internet already. I mean you didn't find us without a search or recommendation and you're probably interested in tech news. But for many casual users, what you might not know is that companies aren't always golden when it comes to your privacy, and in many cases, as long as you don't go looking for the setting to opt-out, block or check "advanced settings" in a website or program, those companies will willingly collect your data.
Below we have an infographic of typical examples that everyday users will come up against, sent in to us by Compliance and Safety LLC.
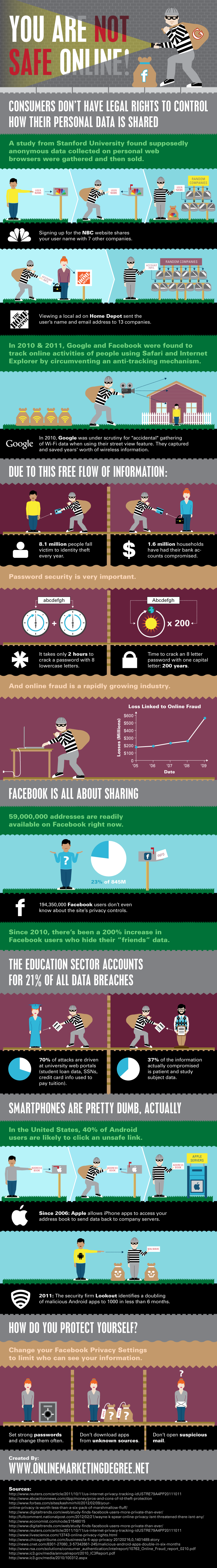
Of course there are ways you can protect yourself by simply educating yourself about the websites and programs you use. Simply diving into the options can already do the trick. Whatever you do, don't rely on most companies to do this for you.
If you're concerned about websites or programs that you use or just want some advice, check out our Internet, Network & Security forum for some helpful feedback by our awesome members.
Source: Compliance and Safety LLC















23 Comments - Add comment