The CCleaner malware fiasco has reached a new height; according to new evidence, the attack may have infected the internal networks of technology giants like Google, Microsoft, and Sony. Initial findings suggest at least 18 such companies were targeted.
Avast, CCleaner developer Piriform's parent company, detailed its progress on the malware investigation in a blog post. In its analysis, the company found evidence in that the malware has successfully sent a 2nd-stage payload to 20 machines in 8 organizations.
Although Avast didn't disclose the names of the victims, 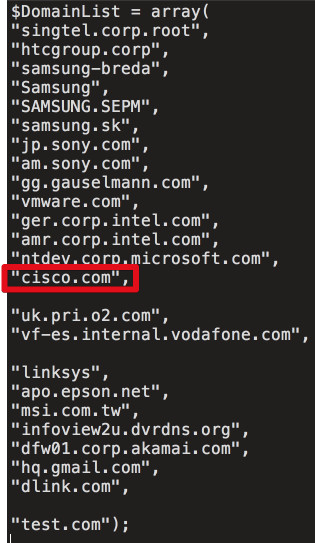 one of the affected firms, Cisco's research group, has identified 18 companies whose names appear in the list of domains communicated by the malware's command and control (C2) servers. It is possible more companies were targeted.
one of the affected firms, Cisco's research group, has identified 18 companies whose names appear in the list of domains communicated by the malware's command and control (C2) servers. It is possible more companies were targeted.
For those who don't know, a 2nd-stage payload is a malicious code (payload) that the initial stage (also a malicious payload) executes after downloading the essential bits; it's an advanced technique that attackers use to mask the size and the intent of the malware. In this case, the payload was a set of DLL files that integrates with Windows and sends user information such as IP address and list of software and hardware to the attackers.
The list includes domains like "ntdev.corp.microsoft.com" and "vf-es.internal.vodafone.com" that are used by the employees of the said tech firms. Since there was a 2nd-stage payload, Avast reckons this was a typical watering hole attack where the attackers initially target a large group victims, receive information, and infect only a certain set of entities. In this case, the actual targets were large tech companies and the probable intention was IP theft.
It is now estimated that only 700,000 Windows PCs were affected by the malware, which is down from the earlier estimates of 2.3 million users. At present, it's not clear if any of the aforementioned companies were infected. Researchers and law enforcement are currently working to gather more information regarding the attack.
Source: The Verge | Image via Talos (Cisco)


















23 Comments - Add comment