
Initially submitted to Microsoft on April 23, and fixed only this Patch Tuesday, CVE-2018-8140 represents three different vectors of attack that use vulnerabilities in Cortana for various nefarious purposes, such as retrieving confidential information, logging into a locked device and even code execution from the lock screen.
The simplest of these is due to the perhaps far-too-helpful nature of Cortana. As researchers at McAfee discovered, simply typing in the term 'pas' will cause Cortana to 'helpfully' put forth many of the files on the system that begin with that phrase. Since Cortana relies on indexing for its queries, the end result is that you may be able to access various password files and, depending on whether the matching was done with respect to the title or the contents of the file, be able to see either the full path to the file location or even the contents of the file, respectively.
The more serious attacks include an elevation of privilege, and results from Cortana not taking into account user status when interacting with her on the lock screen. Alongside a slightly more complicated scheme, McAfee shares a rather simple means of changing the log-in credentials from the lock screen itself:
- Trigger Cortana via “Tap and Say” or “Hey Cortana”
- Ask a question (this is more reliable) such as “What time is it?”
- Press the space bar, and the context menu appears
- Press esc, and the menu disappears
- Press the space bar again, and the contextual menu appears, but this time the search query is empty
- Start typing (you cannot use backspace). If you make a mistake, press esc and start again
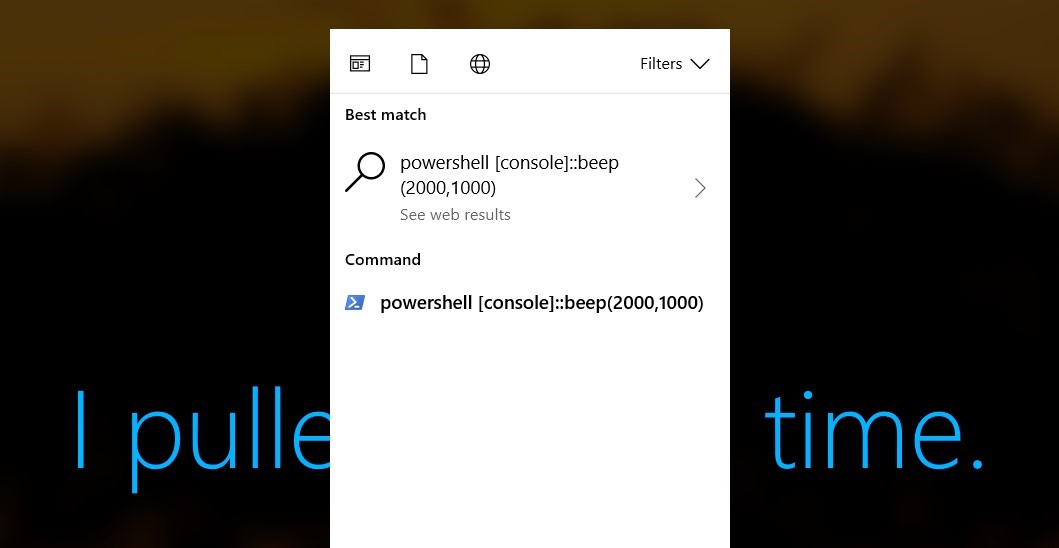
- When done (carefully) typing your command, click on the entry in the Command category. (This category will appear only after the input is recognized as a command.)
- You can always right click and select “Run as Administrator” (but remember the user would have to log in to clear the UAC)
The cybersecurity firm also provided a useful video guide on how the exploit works. Its utility, however, is not limited to changing passwords, and the exploit can be used to execute more powerful and malicious PowerShell scripts right from the lock screen, without even needing to log in. The only requirement is the need to have physical access to the system, so as to allow issuing the digital assistant voice commands.
As mentioned earlier, Microsoft has already pushed a fix for CVE-2018-8140 as part of its Patch Tuesday updates (KB4284819) for June and it's highly recommended you install them as soon as you can. Of course, if you'd like to err on the side of caution, you may also want to consider disabling Cortana on the lock screen.
Source: McAfee via Windows Latest, MSPoweruser




















11 Comments - Add comment