A new variant of the infamous Petya ransomware has been discovered out in the wild, bringing with it old yet nasty tricks to infect a victim's computer, and urge them to pay up.
Dubbed 'GoldenEye,' the crypto-malware is very much identical to the the Petya and Mischa ransomware, which were seen to be bundled together back in May, and were even used for a 'ransomware-as-a-service' system. According to Bleeping Computer, this new malware is spread through spam job application emails in the German language, which contain attachments purporting to be files important to the message.
The first attachment, a PDF file, contains a legitimate-looking resume to make it seem more like the application is genuine. The latter, on the other hand, is an Excel file, and this is where the ransomware's modus operandi kicks in.
Many ransomware variants take advantage of macros found in Word and Excel files. Disabled by default, the malware creators urge the unsuspecting victims to enable the macro feature to be able to "view" the content of the file properly. However, in reality, macros are powerful enough to execute programs which may harm a system's security.
In this situation, clicking on "Enable Content" on the prompt will enable the installation of the GoldenEye ransomware. Once done, it will start encrypting files, and will append a random 8-character extension on each one it targets. It also modifies the boot process of the system, making the computer practically unusable.
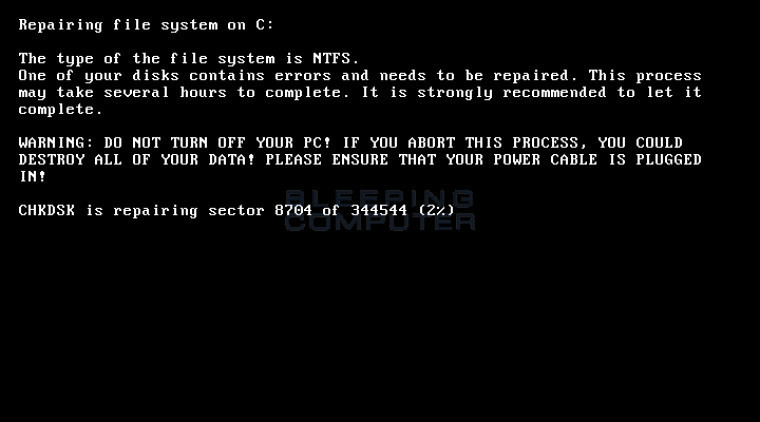
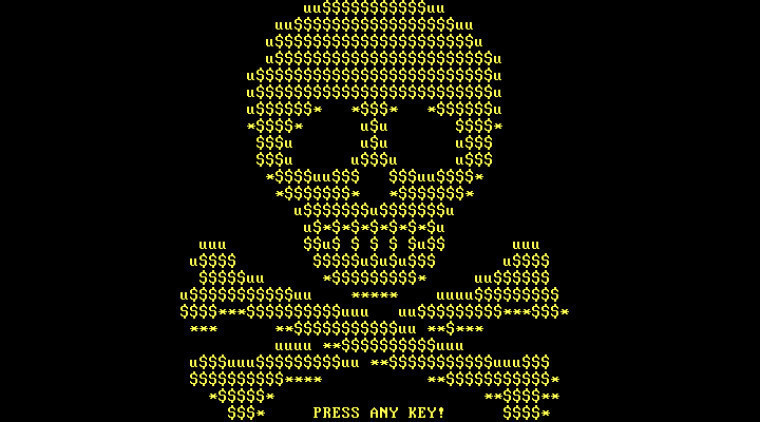
Once it has displayed the ransom note, the ransomware will forcibly reboot the system. It will now display a fake CHKDSK screen, where it pretends to repair issues in the victim's hard drive. After this process is complete, it will display a skull and crossbones screen, much like the one on Petya.

To be able to recover the files, the victim must now enter their personal key to a portal provided, which will ask for 1.33284506 bitcoins, equal to $1,019. The cybercriminals have also provided a support page to help victims with the payment or decryption process should they need any help.
As of the moment, there is no known way to recover files encrypted by the GoldenEye ransomware. For now, it pays to be very careful of our activities on the internet, in order for us to stay safe, and not contract any malware that could harm our computer.
Source: Bleeping Computer















2 Comments - Add comment